May 2002
Access Management
Betting on a
Bundle?
Novell's new Secure Access features several AAA components tied
into its formidable eDirectory. But a lack of integration makes this solution
less of a suite and more like a collection of pieces.
BY
Joel M. Snyder
Original article from Information Security's web site
Novell is jumping into the enterprise security space with
Secure Access,
a suite of existing tools that have been enhanced to wrap
around its widely deployed eDirectory server. The release of the Secure Access
infrastructure this spring is part of Novell's grand plan
to revive its fortunes by positioning itself as an enterprise solutions
provider, playing on a global theme that envisions all networks working
together as "one
Net."
Secure Access is
positioned primarily as an enterprise access control and authentication product.
The suite competes in the already crowded field of access control/identity
management solutions with giants like IBM Tivoli (www.tivoli.com) and Computer Associates (www.ca.com) and stalwart enterprise authorization
management providers such as RSA Security (www.rsasecurity.com) and Netegrity (www.netegrity.com).
As an authentication and authorization solution, Secure
Access covers a lot of territory--Web access, single sign-on (SSO),
server-level authentication, VPN, firewall and support for two-factor
authentication tools such as digital tokens and PKI. Secure Access lacks the
integration or centralized management required to make it a heavyweight
contender in the growing AAA (authentication, authorization and accounting)
security space. As Novell works out the integration kinks, select components
in the suite are worth a look for shops already using or considering
eDirectory.
eDirectory and Company
Secure Access encompasses four main application
areas clustered around a central directory of authentication and authorization
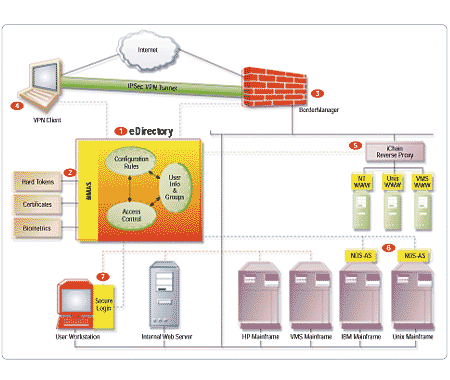
information (see "Secure Access Infrastructure").
Novell has made its eDirectory technology the cornerstone of
the Secure Access suite. This comes as no surprise, since eDirectory is one of
the marketplace's oldest and most respected centralized directories--not to
mention the foundation of Novell's business since NetWare, its once-dominant
network operating system (NOS), was pushed aside by Windows and Solaris.
Novell customers who already
have invested heavily in eDirectory will find this an easy-to-add suite of
solutions that leverages their existing directory and pays off quickly.
However, new customers will want to proceed cautiously.
As a central repository, the LDAP-enabled eDirectory
8.6.1 provides user directory and authentication information, as well as some
or all of the configuration information for each of the Secure Access
components. Although components can also access data in a separate LDAP
directory, eDirectory is always required by each of the Secure Access
tools.
While Secure Access isn't a complete enterprise security suite--there's no
IDS, policy management or AV component, for example--the collection covers a
lot of ground:
Web-based access control. iChain 2.0 is
a reverse-proxy agent that controls access to Web servers. When a request hits
iChain, it uses configuration rules stored in eDirectory to decide who has
access to what. After authenticating the user (if required), iChain passes the
request to the Web server it protects.
Single sign-on. SecureLogin 3.0 is a
workstation agent that intercepts the login process of applications and
provides a virtual SSO service. The general idea is that the end user signs on
once to SecureLogin, which then logs him into various applications as needed.
SecureLogin stores each application's usernames and passwords in the
directory.
A
workstation agent uses a scripting language to detect the windows shown by the
corporate app or Netscape/IE Web browser. This gives SecureLogin enormous
flexibility in the range of NOSes it can work with. However, as we'll see
later, this flexibility comes at a price.
Security managers using SecureLogin can add the Novell Modular Authentication
System (NMAS) from the Secure Access suite, which enables authentication
options beyond the default username/password, such as a smart card that uses
digital certificates.
Server-level integration. NDS
Authentication Services 3.0 (NDS-AS) interacts with agents from non-NetWare
operating systems--including most flavors of Unix, Windows and OS/390 (RACF and
ACF/2)--for user authentication, password checking and password
synchronization. This means that a user can have the same password in
eDirectory that is used for his Unix accounts. And, if he changes the Unix
password, it will automatically propagate back to eDirectory. Novell also
provides direct instructions for integration of the NDS-AS API with other
applications, such as RADIUS servers, Web servers, POP mail servers and SSH.
On the downside, NDS-AS falls short on both the openness of its architecture
and the integration of access management rules.
Firewall and VPN services.
As Novell's combination firewall and VPN solution, BorderManager 3.6 uses
eDirectory for some configuration and access control information.1
As VPN clients try to connect to services inside the corporate network, the
eDirectory says what's allowed.
BorderManager's VPN client is also integrated with
SecureLogin to provide remote SSO. If a remote user is using the VPN client, he
only has to enter his authentication credentials once to get full SSO benefits.
On the other hand, SecureLogin's unique rules engine may involve integration
obstacles, which we'll discuss later.
- eDirectory is at the heart of the Secure Access suite. It
includes user objects, which store authentication information; access control
rules and lists; lists of groups; and configuration information for each of the
other pieces in the suite.
- External authentication services, such as digital tokens,
PKI certificates and biometrics, link into eDirectory via the Novell Modular
Authentication System (NMAS). NMAS enables multi-factor authentication
technology to be used with all of the other components in the suite.
- The BorderManager firewall and security gateway sits at the
boundary of the Internet and the corporate LAN. It controls access,
authenticating users using information stored in eDirectory.
- VPN clients also link to eDirectory, grabbing policy information
and using the directory to authenticate their IPSec tunnels.
- iChain is a reverse-proxy server that protects Web servers on
any operating system (NT, VMS and Unix are shown as examples). iChain uses the
eDirectory for configuration, access control and authentication
information.
- NDS Authentication Services (NDS-AS) run as plug-in pieces on
mainframe computers to synchronize passwords. The plug-ins link back to
eDirectory for authentication information.
- Secure Login resides on workstations, providing single sign-on
to any application on the network (VMS and HP mainframes are shown, as well as
an internal Web server). SecureLogin handles single sign-on by authenticating
users against eDirectory, where application passwords are stored.
Wanted: Better Integration
Novell makes a big deal of
eDirectory as a central repository of information, and also of its ConsoleOne
administration GUI as an integrated management tool. Unfortunately, centralized
management within Secure Access is nonexistent, and this really shows just how
far Novell has to go before Secure Access is a tightly integrated suite. It's
true that Novell never marketed the packages as "integrated"--they're described
as a "bundle." But for Novell to go this far and congregate all of the data
storage in one place without building an integrated data model leaves it
incomplete as an enterprise solution. To grasp what this means, consider this
example, assuming a full Secure Access installation:
- A sysadmin assigning user rights to view a set of pages on a Web server
would expect these rights to propagate to all the tools.
But they don't.
- The admin must access BorderManager's management
interface and define the Web server and its pages as a resource.
- Next, the admin must go to iChain's management
interface and redefine access to the Web server and its pages.
- The user should have SSO authentication to those Web pages,
so the next stop is SecureLogin.
Since resources are often put into groups to simplify management, the
sysadmin would have to manage multiple groups, which might require slightly
different--but still similar--names, to build a reasonable configuration.
Duplicating the data and coordinating the policies across all products is a
complex task and opens the door to configuration mistakes.
Although ConsoleOne's plug-ins have a similar look and feel, they
monitor and
manage different sets of data. This means there's no simple way to ask
questions like, "What does this group have access to?" or "How can I control
the access path to this resource?" What Novell provides is central management,
but not global management.
Novell is certainly aware of this, but offers no timetable or specific
information on how it's going to address it. The company says it's developing a
unified rules engine for all the products in Secure Access, something it learned
from building its ZENworks administration tool. This would help relieve semantic
confusion in administering the components, but until global management with
delegated administration is part of the product, the suite won't fulfill its
potential as an integrated solution.
Configuration management isn't the only concern about the suite's lack of
integration, however. For example, auditing, reporting and logging are all done
on a product-by-product basis. Thus, if an admin wants to track user access to
resources, he would have to look at one or more reports from each of the tools.
eDirectory has basic break-in evasion--such as locking accounts after three
failed logon attempts--to help foil password guessers and brute-force attacks.
However, the different products in Secure Access don't pool their information to
help analyze or deter unauthorized access.
Secure Access also has management issues in its implementation of NDS-AS and
the administration of authorization for individual systems. Generally,
centralized authentication and authorization service components within Secure
Access push a lot of the configuration information into the eDirectory server,
which means each system manager must trust eDirectory for authentication. Under
NDS-AS, we would expect that the network administrator--or admin with delegated
rights--would be responsible for authorization rules. However, since access isn't
controlled centrally but at the host level, this actually falls to the
individual system manager. The system's API is to NDS-AS, not a global rules
engine, because there is no global rules engine. This could be a real burden to
a large organization with numerous systems. Many system managers may prefer this
choice, but Novell should have given the option to keep that information in
eDirectory when adding NDS-AS to the Secure Access suite.
Other Benefits and Shortcomings
The critical question of integration/central management isn't the only factor
in evaluating Secure Access' place in the enterprise access control space. Here
are some other key points to consider:
Directory services. eDirectory is a strong base around which
to build this suite. A number of corporate clients have deployed eDirectory on
Solaris SPARC as the core of huge e-commerce initiatives. In addition to
Solaris, eDirectory currently supports NetWare, Windows NT/2000, Linux and
Compaq's Tru64 Unix.
While OS support is broad, the Windows port of eDirectory has a reputation
for being quite weak from a management perspective. While the core functionality
is intact everywhere, the different management GUI options on the three
different operating environments--NetWare, Unix, Windows--weren't melded smoothly
by Novell. The general operations interface of the Windows port is poorly
constructed, and the Windows version lacks some minor options available under
NetWare. Finally, some Windows managers won't be comfortable navigating
eDirectory because it doesn't feel like a Windows application, but rather a
NetWare application ported to Windows.
Because eDirectory is LDAP compliant, it can be integrated into a non-Novell
environment, despite its proprietary internal structure. While Novell's schema
may not match directly to Internet standards, it's close enough that most
applications running LDAP against eDirectory won't know or care what's on the
other end of the pipe.
Since user authentication information is stored in eDirectory, other security
applications that talk to eDirectory via LDAP can be used to centralize some
access control information. This can be misleading, though. Just because two
applications use the same directory doesn't mean they use the same data in the
same places. The danger is the possibility of duplicate information in a single
directory. On the other hand, it may be better to have duplicate information in
one directory rather than have two different directories to manage.
Web access control architecture. One thing we
discovered when analyzing similar suites (see
"Authorization: The New Holy
Grail?")
was the tremendous variation in architecture and technology chosen by each
vendor in the access management space. As noted earlier, some products, like IBM
Tivoli's Policy Director, use proxies in an architecture similar to Novell.
Others, like RSA ClearTrust, push control out with a combination of plug-ins and
database replication. Each choice has its advantages.
Because iChain is a proxy, it offers some of the usual features of proxy
servers, such as internal caching to speed throughput and SSL acceleration. It's
not, however, designed primarily as a proxy product, so it misses some features,
such as application-level (Layer 7) load balancing and switching.
The obvious benefit is that the reverse proxy is totally independent of the
choice of Web server. On the downside, proxies can also interact negatively with
Web content on servers, particularly dynamic content.
However, access control packages that are integrated with popular Web servers
have other benefits. Total system reliability is higher, because fewer systems
are in the picture. And products like Netegrity's SiteMinder push authentication
information all the way to the server, which lets Web application developers
efficiently use the identity information to personalize content. For example,
this architecture allows for a custom Web interface that shows only three of a
possible five radial buttons to a particular user, limiting his access to
enterprise resources. (Netegrity has also released an add-on product, SiteMinder
Secure Proxy Server, which offers reverse-proxy architecture as an option.)
OS requirements. All of the components of Secure Access can
be run on most operating systems--NetWare, Windows, Solaris and other Unix
variants--with one very significant exception.
NDS-AS is the laggard when it comes to Novell's open architecture. At press
time, NDS-AS requires a NetWare server for proxy communications between agents
on guest OSes and the master directory. Customers new to Novell almost certainly
won't want to learn NetWare to support Secure Access. Novell says the next
release of NDS-AS, expected this month, will support the engine on NetWare,
NT/2000/XP, Solaris and Linux and have drivers/agents for NT/2000/XP, Solaris
SPARC, Solaris Intel, HP-UX, AIX, Linux, FreeBSD and OS/390 (RACF and ACF/2).
Another update, scheduled for later this summer, will add support for AS/400,
Tru64 Unix and OS/390, according to Novell.
Single sign-on. Because SecureLogin is client-based rather
than server-based, it has the advantage of being able to work with a wide
variety of NOSes. However, if an organization only has a small number of
operating systems and a lot of different applications, the tradeoff becomes
clear: each application has to be individually scripted to handle its unique
authentication dialogs. This isn't necessarily a bad thing, but it means that
network managers will have to engage with each application.
The good news is that SecureLogin includes support for more than 30 terminal
emulators. The bad news is that SecureLogin runs on only Windows 98/ME and
NT/2000 workstations. Novell, a long supporter of the underdog in the OS wars,
completely left Macintosh (and Unix) users out of the desktop picture. Of
course, Novell's answer to this shortcoming is stock for the industry: "If we
have customers come to us who are willing to pay money, we'll do anything."
Firewall. BorderManager is poorly integrated and saddled
with obsolete technology. The rules engine executed by BorderManager is
different from other components, so manual synchronization is required. For
example, a firewall could fit in nicely with the Secure Access security scheme
by sitting as a gateway in front of iChain proxies. But BorderManager can't
share any authentication information with other pieces of the Secure Access
suite, so it can't control access to iChain.
Novell is also propping up an aging and unpopular firewall. While Novell's
loyal fans continue to use BorderManager, its clumsy configuration places it a
generation behind the state of the art in enterprise firewall technology.
BorderManager alone would be a highly unlikely choice for anyone not already
heavily committed to NetWare.
Selling Points
Novell's main claim is that deploying Secure Access to
enforce consistent policies across multiple authentication and authorization
applications will bring three benefits:
Savings. Cost will be reduced in
several ways, including reduced application development time, faster user login
and fewer help desk calls dealing with password resets and authentication
issues.
Of these, help desk relief is one of the most obvious savings to help justify
the suite's $159 per user price tag. If an enterprise can reduce the number of
passwords to be learned--and forgotten--from 10 or even 20 down to one, total help
desk costs will certainly go down.
Security. Total system security will be improved by building a comprehensive
authentication system. Any piece of Secure Access can certainly make this claim
with justification. Having a well-secured SSO application that uses long and
random passwords to log on to a dozen or more other applications is going to
reduce risk, which in turn increases security. The same is true of iChain: If an
organization can build an inexpensive authentication and authorization system in
front of all Web servers, each application developer can concentrate on the Web
application rather than how to secure access. A single framework will both
increase security and reduce application development costs.
User satisfaction. Novell claims that Secure Access will make end users
happier. Security managers who have long been the whipping boys for corporate
complainers will certainly perk up at this idea. Based on our analysis, Novell
has an excellent chance of winning this argument. If users can apply strong
authentication technology to their jobs without having to log in to a dozen
different applications with a dozen different usernames and passwords, they
definitely will be happier.
The Big Picture
Novell has done more than propose its eDirectory as a central repository for
data. Secure Access, if fully implemented, would have Novell software on every
desktop in the enterprise, with Novell also manning the gates in front of Web
servers, handling the firewall and even digging into IBM mainframe
authentication arcana. That's a pretty heady proposal for a company that has
often been considered a niche player in the security market.
Clearly, Novell has the chops to do this. Through its years of battling
against Microsoft for NOS supremacy, Novell has learned how to integrate tightly
into Microsoft's desktop OSes. When it comes to authentication hooks, Novell was
there first and has more experience than anyone.
Companies
like Computer Associates and IBM, which also have jumped into the authentication
suite business, may or may not be able to match Novell's experience in this
area, or even the limited integration Novell has achieved. While CA has made a
business of acquiring excellent point solution providers and integrating them
into a consistent framework, its track record with users accepting a broad range
of CA products as a single suite has not been very good. Customers buy the
parts, but they have not fallen in love with the whole.
However, as mentioned
earlier, there's a lot of competition in the access control/identity management
solution space. Though Novell may be unique in bundling firewall/VPN services,
it's going up against the likes of Netegrity, Entrust (www.entrust.com), Blockade Systems (www.blockade.com), Entegrity (www.entegrity.com), Baltimore Technologies (www.baltimoretechnologies.com),
Oblix (www.oblix.com), RSA Security
and BMC Software (www. bmc.com), among others.
Novell customers who already have invested heavily in eDirectory will find
this an easy-to-add suite of solutions that leverages their existing directory
and pays off quickly. However, new customers will want to proceed cautiously.
Until Novell really integrates the products within Secure Access, each piece
needs to be evaluated individually for its suitability as an independent point
solution. Because Secure Access will always require some piece of eDirectory at
the core, jumping on the Novell bandwagon could be an expensive proposition for
organizations that already have a large investment in LDAP or X.500 directory
services.
But keep an eye on this suite. If Novell moves successfully from "bundle" to
"integration," Secure Access has the potential to be a tier-one competitor.
JOEL SNYDER
is a senior partner at Opus One, an IT consulting
firm in Tucson, Ariz.
